Zero Trust As-A-Service
Mitigate & stop Cyber Attacks with a Zero-Trust Philosophy
If it’s not approved as trusted, it’s not allowed
Enables Zero-Trust Application Access As-A-Service allows for ease of Application Control adoption and restriction of local admin rights, mitigating and stopping cyberattacks from happening.
Zero-Trust is the foundation of security frameworks
The Essential 8 Framework should be an integral part of any Australian Business Cyber Security Strategy and Application Control is a good place to start, restriction of local admin rights on computers goes hand-in-hand with Application control to deliver a complete solution.
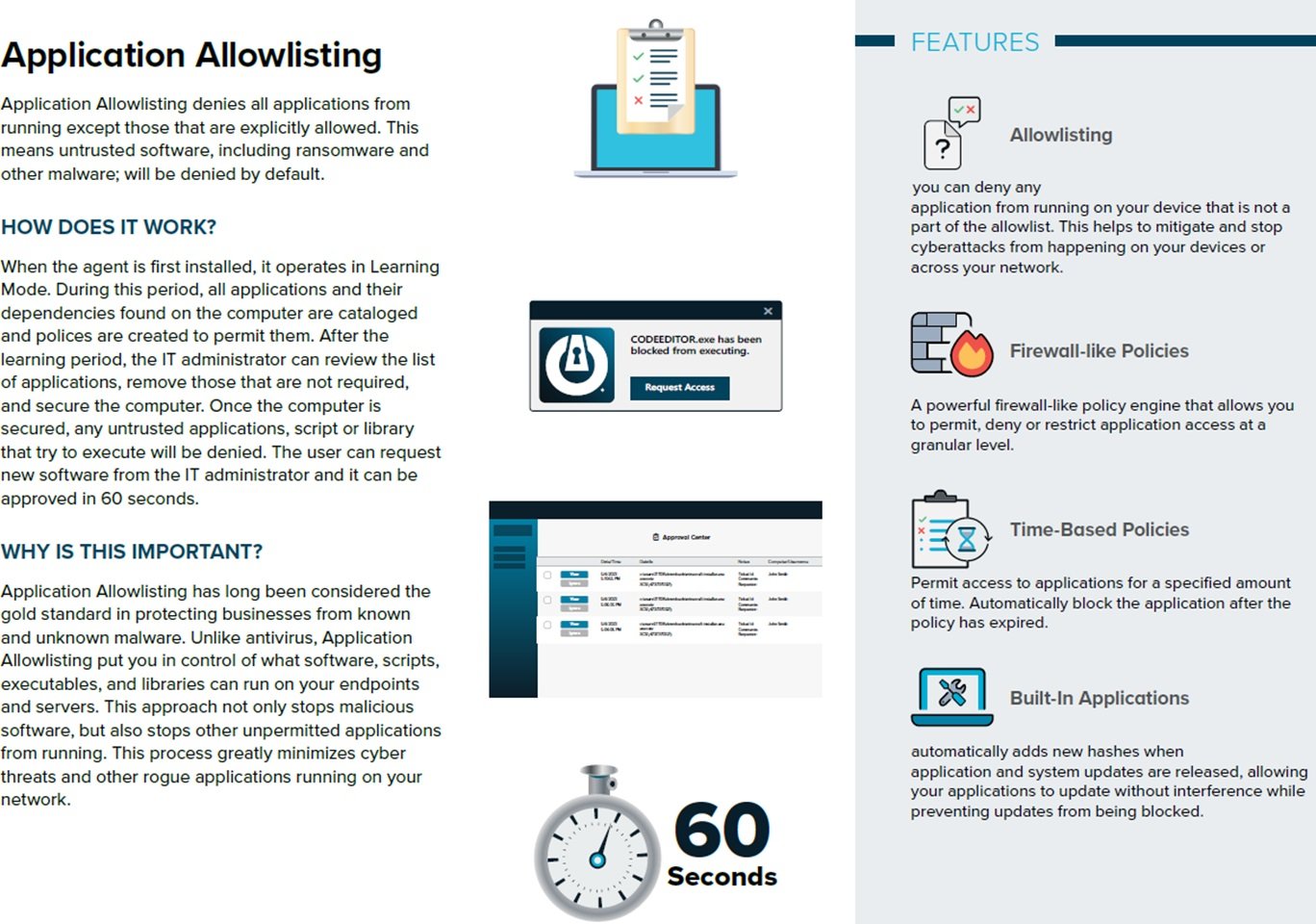
Application control is a powerful security strategy that many organisations use to protect critical assets. On a device or network that uses an application control, only specific, pre-approved applications are allowed to run. This prevents users from running malicious software, such as viruses, malware, and ransomware, which can compromise the security, confidentiality, integrity, or availability of a business’s systems.
Our Zero Trust endpoint protection offering provides enterprise-level cybersecurity. Instead of relying heavily on detection methods and chasing threats, our solution blocks everything that is not explicitly trusted and limit actions to only what is needed.
“Zero Trust security is much more effective than detection tools.”
The Zero Trust philosophy extends beyond Allowlisting to incorporate controlling what permitted applications can do, what storage areas can be accessed and how, and what network connections can be made. Denies and allows are recorded in real time in a Unified Audit to assist with compliance and utilises this real-time data to alert you of any blocked malicious action.
The Zero-Trust endpoint protection offering is designed to be easy to use and integrate seamlessly into existing IT environments.